The standard Linux permissions are suitable for most situations but they have their own limitations. The standard permissions limit access to file owner, group owner and others. But, what-if we want to grant specific permission to another named user, other than the user-owner or another named group other than the group-owner. Access Control List (ACL) allows us to set these fine-grained permissions.
Consider an example:
For the file data.txt

user-owner is baljit, having permissions rwx
group-owner is Linux having permissions rw-
others have permission r–
Now, can we grant a named-user Ricky, rw- permissions on this file (without making him the user-owner)?
Can we grant another named-group Guest, rwx permissions on this file while keeping the group-owner same?
To achieve these, we have to use Access Control List and learn the use of setfacl and getfacl commands.
How to view ACL – getfacl
The ls -l command shows minimal ACL settings. A ‘+’ sign at the end of the permissions means that ACL is set on the file or directory.

- + : means ACL is set
- user: shows user ACL settings, which are same as standard user file settings
- group: shows current ACL mask settings, and not the group-owner settings
- other: shows other user ACL settings, which are same as standard other file settings
So, the best way to view ACL settings is to use the getfacl command

Information:
#file : name of file/directory (practice)
#owner: name of user-owner (Rohit)
#group: name of group-owner (Linux)
user: User-owner permissions (rw- for Rohit)
user:Virat: permissions for named-user Virat (none)
group:Group-owner permissions (r– for members of Linux group)
group:project1: permissions for members of named-group project1 (rw-)
mask: maximum effective permissions for group-owner, named-group and named-user (rw-)
other: permissions for others (r–)
How to Set ACL permissions – setfacl
The setfacl command is used to add, modify or delete standard ACL permissions on files and directories.
Permissions Flags
- r – read
- w – write
- x – execute
- – – permission is absent
- X – means execute is set on sub-directories and not regular files (unless the files already has execute permission). Used while setting Recursive ACL on directories
Adding or Modifying ACL
Add or modify a user or named user ACL
$setfacl -m u:name:permissions file
If the name is kept empty, the permissions are applied to file-owner. The name can be username or UID.
Note: ACL user-owner and standard user-owner settings are equivalent. So, using chmod and setfacl to change user-owner permissions will have the same effect.
Example:

Add or modify a group or named group ACL
$setfacl -m g:name:permissions file
If the name is kept empty, the permissions are applied to group-owner. The name can be group-name or GID.
Note: chmod has no effect on any group permissions if ACL is set on the file or directory. chmod will update the ACL mask. So, to change group permissions if ACL is set use the setfacl comamnd only.
Example:

Add or modify other ACL
$setfacl -m o::permissions file
Note: ACL other and standard other settings are equivalent. So, using chmod and setfacl to change other permissions will have the same effect.
Recurring ACL for Directory
Recurring ACL are used when you want to change the ACL settings for all the files and sub-directories along with those of the directory itself.
Before setting Recursive ACL

After setting Recursive ACL
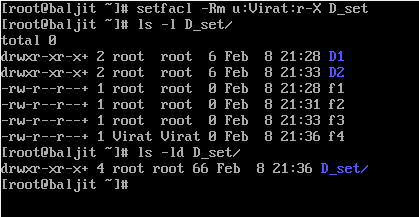
It is clear from the output that ACl is set on the directory D_set as well on the files and sub-directories within it. Another point to note here is the use of ‘X’ while setting ACL. Using ‘X’ will give execute permission on all sub-directories but not on regular-files (unless if already exists)
Setting Default ACL for Directory
Recursive ACL works on on existing files and directories. For setting default ACL settings for future files and sub-directories that you want to create use
$setfacl -m d:u:name:permission directory $setfacl -m d:g:name:permission directory
Note: While setting default ACL on a directory, ensure that the users get execute permission on the new directories otherwise they will not be able to access the directory content. So, use ‘X’ as a permission
Example: In the below example, default ACL is set on D_set directory which allows Virat user read and execute permission. The same is verified by creating a new file and viewing its ACL settings

Setting Explicit ACL Mask
An explicit mask can be defined for named-users, group-owner and named-groups. Mask will restrict any permission that exceed the mask i.e., even if a named-group has higher permission than the mask it will not be able to use those. For example,

The mask set is r– on D_set directory. Now, even though the named-group project1 is having rwx permissions but the members of project1 will only be able to read the contents. That’s why the #effective:r– comment is written in front of named-user, group-owner and named-group.
Deleting Access Control List (ACL)
To delete a particular ACL setting use the -x option
$setfacl -x u:name file
$setfacl -x g:name file
To delete all ACLs at once use -b option
$setfacl -b file
Practice Question on Access Control List (ACL)
Consider a directory Linux. Only, members of Section group have access to this directory. Now, assign full permission to Class group also. Manoj, a member of the Class group, has misbehaved and it has been decided that he be denied access to the directory.
Your task is to assign the appropriate ACLs to Linux and its contents, so that members of Class group have full access except Manoj who is denied any access. Also, ensure that future files and sub-directories inside Linux get appropriate ACLs applied.
PPT on ACL
Video Link
Relevant Topics to Access Control List (ACL)
useradd
groupadd
How to change file permissions using chmod command in Linux?