Let’s start with a scenario
Before getting into the theory about What is SELinux? Let’s try to understand the use of SELinux by taking an example.
To host any webpage using the httpd web service we create the web pages in /var/www/html directory. So create one sample web page named index.html in /var/www/html and write the following content in it.
This is a sample web page hosted in /var/www/htmlMake sure the httpd service is running.
#yum install httpd
#systemctl start httpd
#systemctl enable httpdNow, open your web browser and host the above-created web-page

The localhost in the web address refers to the Document root which is defined in the httpd configuration file (/etc/httpd/conf/httpd.conf)
Similarly, you can create any other web page in /var/www/html and try hosting it.
Now, create a directory /test and a web page inside it /test/myweb.html. Also, write some content inside the file.
#mkdir /test
#touch /test/myweb.htmlNow, move this to /var/www/html
#mv /test/myweb.html /var/www/htmlNext, try hosting this web page on the browser. But this time you will get an error as shown below.

Check the permissions on the files. Although the permissions are exactly same but still the web server is not able to host the file myweb.html. Why?
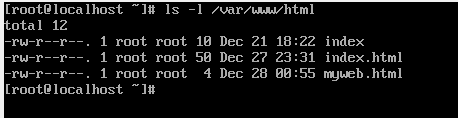
The answer is SELinux. SELinux prevents any file not having the permissible context to be hosted. Use the ls -lZ command to view the context on the files.

Note that the context of myweb.html is default_t whereas, for all files that you were able to host, the context is httpd_sys_content_t. The web server is allowed to access only those files which have the context httpd_sys_content_t. All this has been defined in SELinux policy by the developers.
What is SELinux?
Security Enhanced Linux or SELinux is a feature in Linux systems that enables the administrators to have additional control over who can access the system. SELinux establishes access controls for a system’s applications, processes, and files. To enforce the access granted by a policy, it employs security policies, which are a collection of rules that instruct SELinux what can and may not be accessed.
The most significant ideas in SELinux are type enforcement and labelling. SELinux is a labelling system, which implies that every file, process, and port in a system has a SELinux label attached to it. Labels are a rational manner of categorising something. During startup, the kernel maintains the labels.
User:role:type:level is the format for labels (level is optional). In more complex SELinux implementations, such as MLS, user, role, and level are utilised. For targeted policy, the label type is the most significant factor. To enforce a policy established on the system, SELinux utilises type enforcement. The component of a SELinux policy that determines whether a process running with a specific type may access a file tagged with that type is called type enforcement.
SELinux Modes
SELinux has three modes:
- Enforcing – SELinux protects any unauthorized access. It maintains log and protects.
- Permissive – SElinux allows all interactions even if no explicit rule exists. It only maintains logs but does not protect.
- Disabled – SELinux is completely disabled. It neither protects not maintains logs.
Changing SELinux Modes
getenforce – The getenforce command shows the current SELinux mode
#getenforcesetenforce – command changes the mode from Enforcing to Permissive and vice-versa. An example is shown below:

To disable SELinux setenforce command can not be used. To disable SELinux you need to edit the configuration file /etc/sysconfig/selinux. Remember, to reboot the system after updating the configuration file.

Change the highlighted line, SELINUX=enforcing to SELINUX=disabled.
Save the changes and reboot the system. Rebooting the system is necessary to implement the change.
Next
Video Link
Relevant Topics
chmod command
ACL (Access Control List)